Third-party IdP SSO integration
NAVIGATION Header > Admin Settings > Single Sign-On
PERMISSIONS Master role
KaseyaOne supports third-party identity provider (IdP) single sign-on (SSO) integrations, (such as Okta or Microsoft Entra ID) to centrally manage your users allowing them to access KaseyaOne via SSO if it supports SAML 2.0.
The integration between KaseyaOne and third-party IdP allows users to log in to KaseyaOne from both the IdP interface and the KaseyaOne login page using the IdP credentials. This reduces the amount of user credentials in use and streamlines the login process. You can also add an extra layer of security by forcing users to log in to KaseyaOne from the IdP only.
You manage your third-party identity provider SSO integration and the following SSO-related features on the Single Sign-On page:
- Enforce Log In with SSO. This forces users to log in with their SSO application.
- Enable Automatic User Creation. This allows just-in-time provisioning for the third-party IdP SSO application so that user accounts are automatically created with a specified default role when new users authenticate for the first time.
- IdP Groups Access Control. This allows you to control user access for third-party IdP SSO users.
How to...
NOTE Before running this procedure, you must create and configure the KaseyaOne SSO application in the third-party IdP. For details, see Setting up a third-party IdP SSO integration for KaseyaOne below.
To configure SSO in KaseyaOne for third-party IdP integrations (such as Okta or Microsoft Entra ID) so that users will be able to authenticate using the third-party IdP:
- Navigate to the Single Sign-On page. Refer to Security and navigation.
- In the Single Sign-On with Identity Providers section, click Add configuration.
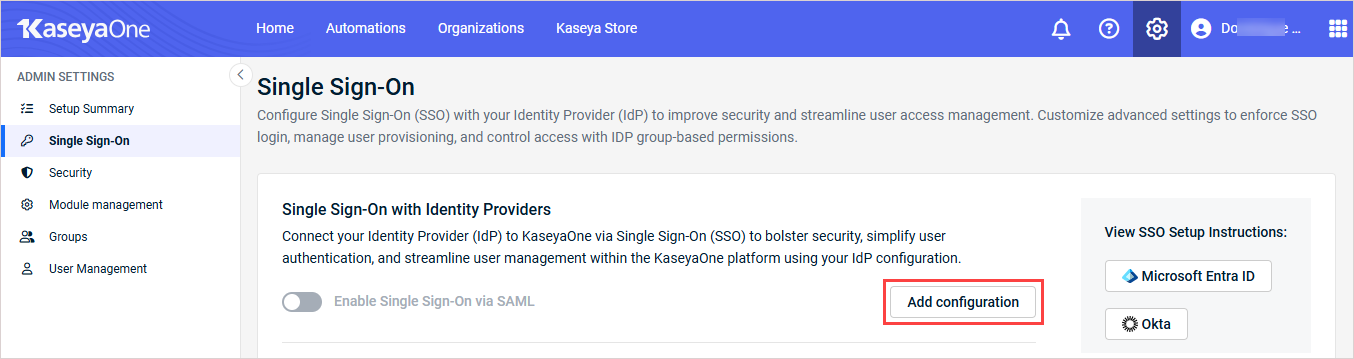
- Enter the following information:
- Identity Provider Single Sign-On URL: Enter the third-party IdP SSO URL in this field.
- Identify Provider Issuer: Enter the third-party IdP issuer in this field.
- Click Upload Certificate to upload the third-party IdP certificate. Enter the Certificate Information.
- Click Save.
- In the Single Sign-On with Identify Providers section, turn on the Enable Single Sign-On via SAML toggle to enable SSO via SAML for the IdP.
- Click Save. You will see a check mark and the word Configured after successfully configuring SSO.
NOTE Secure Assertion Markup Language (SAML) provides a way to authenticate users once and then communicate that authentication to multiple other applications.
- Configure one or more of the following Advanced Single Sign-On Settings as required:
- Enforce Log In with SSO to force users to log in with their SSO application. Refer to Configure Enforce Log In with SSO in KaseyaOne.
- Enable Automatic User Creation to allow just-in-time (JIT) user provisioning for the SSO application. Refer to Configure Enable Automatic User Creation for a third-party IdP SSO in KaseyaOne.
- IdP Groups Access Control to control access to KaseyaOne using your IdP group user assignments. Refer to Configure third-party IdP Groups Access Control in KaseyaOne.
IMPORTANT Advanced Single Sign-On Settings cannot be enabled until Enable Single Sign-On via SAML is configured and enabled.
NOTE Currently, only one third-party IdP integration can be active in KaseyaOne.
A valid certificate is needed for SSO functionality between KaseyaOne and your third-party IdP. SSO certificates typically expire in two years. To prevent login disruptions, you must upload a new certificate before your existing certificate expires.
When will my certificate expire?
KaseyaOne notifies all Master users when an SSO certificate is nearing expiration: at 60 days before expiration, 30 days before expiration, seven days before expiration, on expiration day, and one day after expiration. These notifications display in the KaseyaOne UI and are also emailed to Master users. Notifications cease once a new, valid certificate has been uploaded. Example notifications are shown here: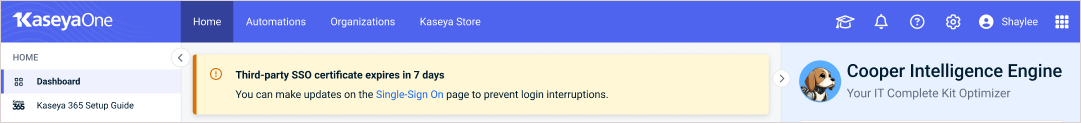
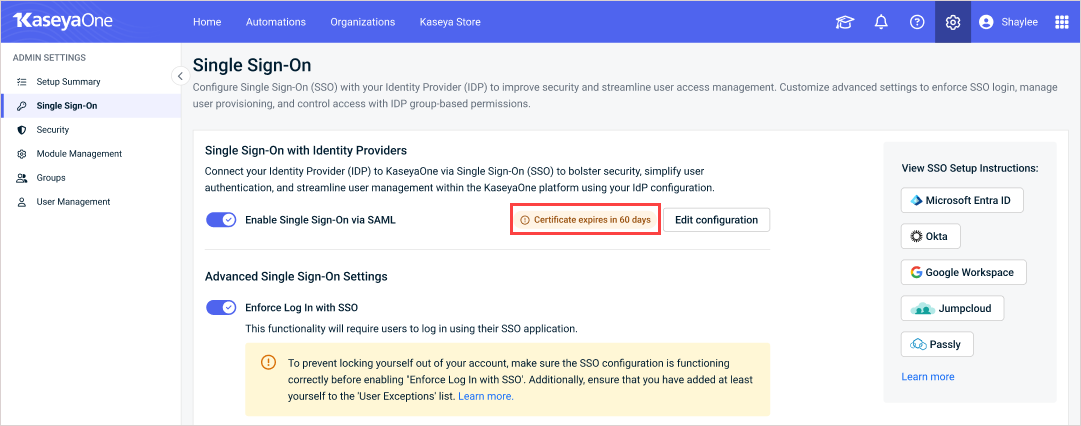
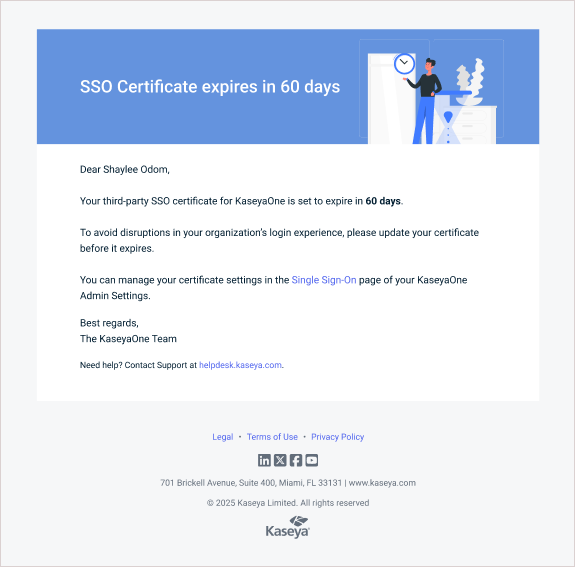
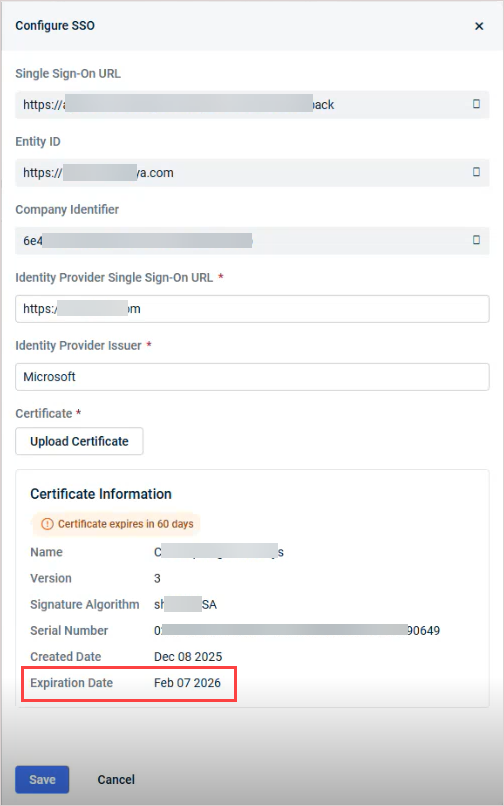
You can also check the certificate's expiration date by viewing your third-party IdP's configuration from the Single Sign-On page.
To upload a new certificate
- Navigate to the Single Sign-On page. Refer to Security and navigation.
- In the Single Sign-On with Identity Providers section, click Edit configuration.

- In the Configure SSO pane, click Upload Certificate, browse to select the new certificate, then click Open to upload.
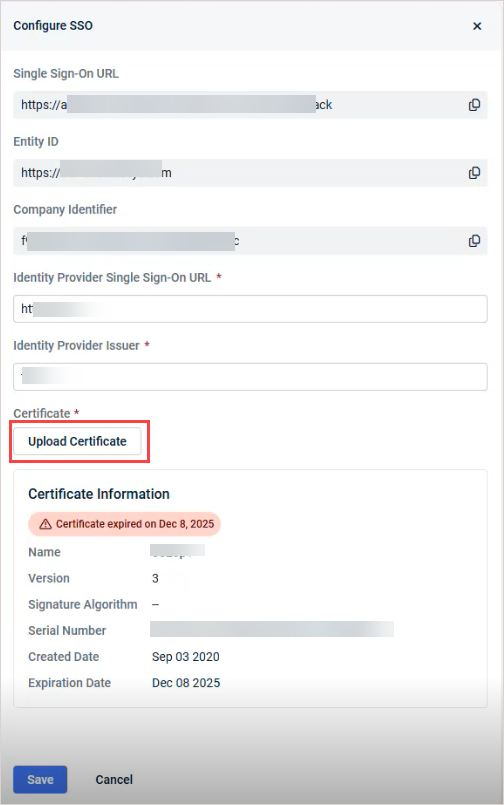
- You see a Certificate uploaded successfully message and details of the new certificate display in the Configure SSO pane. All certificate expiration notifications are removed from the KaseyaOne UI.
You can configure Enforce Log In with SSO functionality as shown in the following procedure to require users to log in to KaseyaOne with their SSO application.
NOTE This functionality cannot be enabled until Enable Single Sign-On via SAML is configured and enabled.
- In the Advanced Single Sign-On Settings section, turn on the Enforce Log In with SSO toggle to enable the feature.
- If enabled, users are forced to log in to KaseyaOne with their SSO application (and prompted to do so).
- If disabled, users are allowed to log in to KaseyaOne using either their SSO application or local authentication.
- From the User Exceptions drop-down menu, select one or more users who will be exempt from the Enforce Log In with SSO condition, if enabled.
NOTE To prevent locking yourself out of your account, make sure the SSO configuration is functioning correctly before enabling Enforce Log In with SSO. Additionally, ensure that you have added at least yourself to the User Exceptions list.
NOTE Users enabling Enforce Log In with SSO in KaseyaOne, if not a Master Root user, are notified that they have been added to the User Exceptions list, with the option to remove themselves.
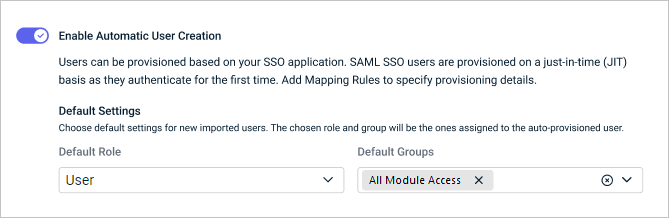
You can configure Enable Automatic User Creation as shown in the following procedure to enable just-in-time provisioning (JIT) for the SSO application. SAML SSO users will then be provisioned on a just-in-time basis with a specified default role when they authenticate for the first time.
JIT provisioning increases efficiency and productivity, saves time and resources, and reduces administrative costs. It allows new users to access a web application in real-time, eliminating the need for manual account setup.
The prerequisites to using JIT provisioning for third-party IdP SSO are:
- You must have SSO to enable this function. Configure the SSO connection and settings for the IdP and toggle on Enable Single Sign-On via SAML in KaseyaOne. Refer to Setting up a third-party IdP SSO integration for KaseyaOne.
- Preconfigure the user role and groups before turning on this feature.
To configure Enable Automatic User Creation for third-party IdP SSO in KaseyaOne:
-
In the Advanced Single Sign-On Settings section, turn on the Enable Automatic User Creation toggle to enable the feature.
- In the Default Role field, click the drop-down arrow and select one role to assign to auto-provisioned users. You can select Master, Billing, User, or Co-Managed User.
- In the Default Groups field, click the drop-down arrow and select one or more group(s) where auto-provisioned users will be assigned.
- Changes are automatically saved.
You can configure role-based access control (RBAC) for third-party IdP SSO users in KaseyaOne. This involves enabling the IdP Groups Access Control feature for third-party IdP SSO and then defining mapping rules to control user access for SSO users as shown in the following procedure. The purpose of defining mapping rules is to mimic or maintain the same levels of user access defined in the third-party IdP and port them over to KaseyaOne.
IdP Groups Access Control provides automatic correct user permission assignments based on IdP groups. This streamlines user management and reduces the time spent on it. IdP Groups Access Control ensures that the correct permissions are automatically assigned to the users that are coming from IdP based on their IdP group memberships.
IMPORTANT Currently, IdP Groups Access Control only works if Automatic User Provisioning is enabled.
NOTE IdP Group Access Control cannot be enabled until at least one Mapping Rule is enabled and Enable Single SIgn-On via SAML is enabled.
Prerequisite
-
Ensure that the group names specified in the mapping rules are an exact match with your IdP Group Names.
To configure IdP Groups Access Control for third-party IdP SSO in KaseyaOne:
- In the Mapping Rules section, select either Stop at first match or Process all rules.
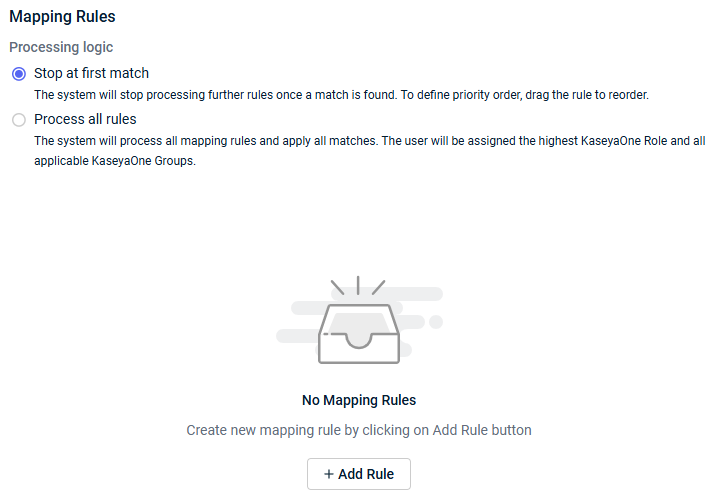
- Click Add Rule.
- Enter the exact name of the third-party IdP user Group Identifier in the IdP Group Name field. IdP group names are case-sensitive.
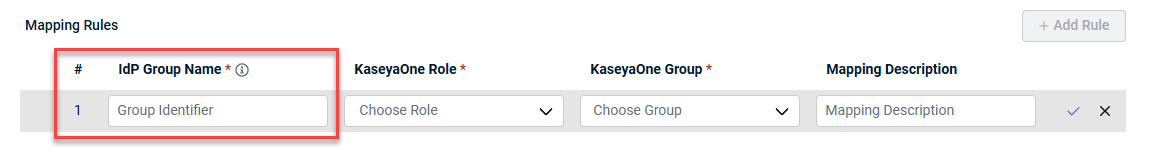
NOTE If you are configuring Microsoft Entra ID, please use Group Identifier instead of Group Name. For example, a2e68765-f908-453c-a31b-************).
- Select one KaseyaOne Role from the drop-down list. You can map an IdP group to more than one KaseyaOne Role.
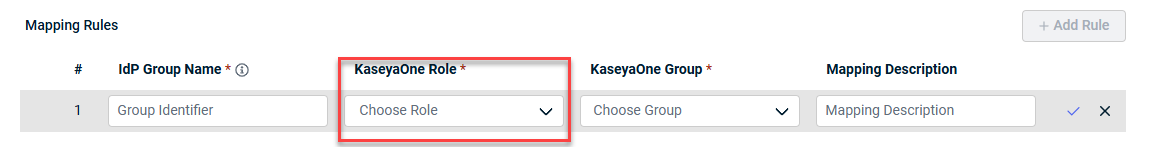
- Select a KaseyaOne Group from the dropdown list. You can select more than one KaseyaOne Group.

- (Optional) Type in a description of the mapping rule in the Mapping Description field.
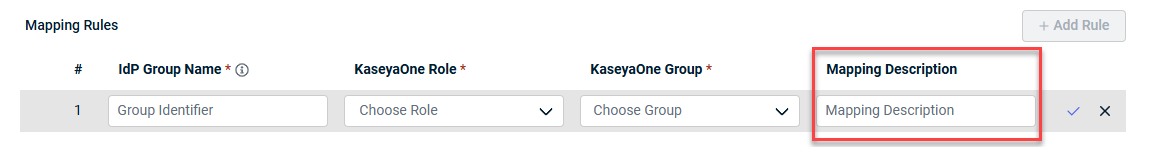
- Hover over the mapping rule and drag to reorder.
- Turn on the IdP Groups Access Control toggle to enable the RBAC feature for SSO users.
- Click the Save check mark.
IMPORTANT If a user does not belong to the IdP group or the IdP group is not defined in the Mapping Rules, the user's KaseyaOne account will be deactivated and revoked access to KaseyaOne.
NOTE Any mapping rule(s) that you define here will override the default role specified in Configure Enable Automatic User Creation for a third-party IdP SSO in KaseyaOne.
Setting up a third-party IdP SSO integration for KaseyaOne
The overall process to set up a third-party IdP integration using SAML 2.0 for KaseyaOne is similar across all IdPs and involves the following tasks:
- Create and configure the KaseyaOne SSO application in the third-party IdP. For this task, you will need to copy the Single Sign-On URL and Company Identifier for your KaseyaOne instance from the Single Sign-On page in KaseyaOne, as shown here:

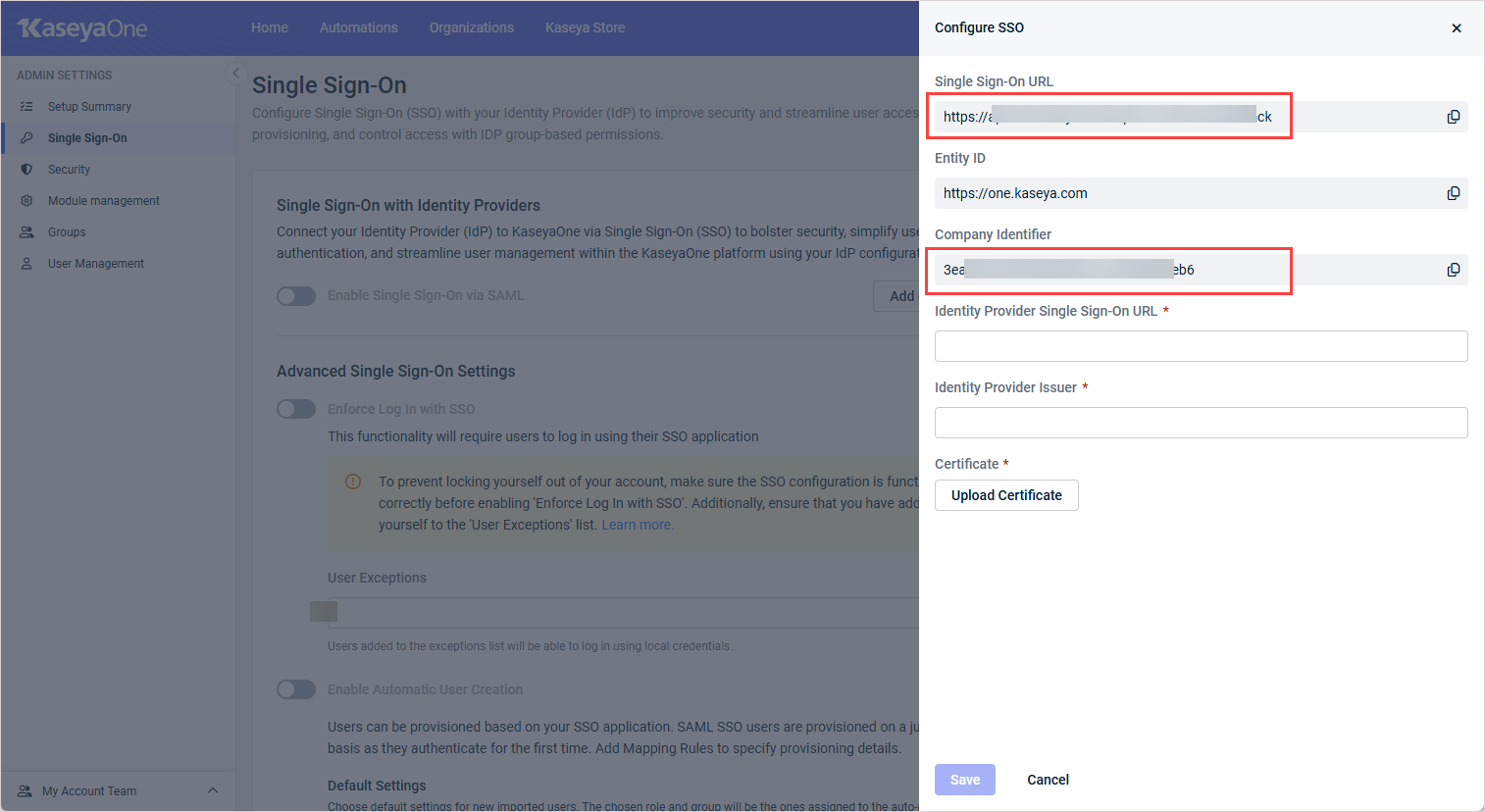
Once you've obtained your KaseyaOne Single Sign-On URL and Company Identifier, you can configure KaseyaOne SSO in your third-party IdP. (See Third-party IdP SSO integrations using SAML 2.0 with KaseyaOne below for detailed instructions for commonly used third-party IdPs.)
- Configure the SSO settings in KaseyaOne for the third-party IdP integration. For this task, you will need the third-party IdP's Single Sign-On URL and SSO certificate. Once you've obtained the third-party IdP's Single Sign-On URL and SSO certificate, use this procedure to configure SSO settings in KaseyaOne: Configure SSO in KaseyaOne for a third-party IdP integration
- Assign users to the KaseyaOne application in your third-party IdP so that they will be able to use it.
- Test the third-party IdP SSO integration for KaseyaOne.
The prerequisites to set up a third-party IdP integration with KaseyaOne are:
- A KaseyaOne user account with the Master role and an administrator account in the third-party IdP.
- Users must have the same email address in KaseyaOne and the third-party IdP.
- User/user groups must be set up in the third-party IdP.
After you set up the third-party IdP integration, the next time you log in to KaseyaOne you will be prompted to select your preferred method to log in — sign in with Single Sign-On or with your KaseyaOne credentials, unless Enable Single Sign-On via SAML is enabled. We recommend referring to your IdP's documentation when configuring this feature as they will provide the most up-to-date documentation for their platform.
Third-party IdP SSO integrations using SAML 2.0 with KaseyaOne
Set up third-party IdP SSO integrations with KaseyaOne: